Today I’m bringing you a post that’s all about Dynamics 365 F&O, but the main focus is on security, specifically Microsoft Sentinel. Some days ago it was announced a Microsoft Sentinel Solution for F&O had been published and is currently in preview. Let’s learn a bit about it!
Sometimes we overlook the security aspects of the things that are not directly related to F&O, specially regarding resources like networking, storage accounts, dev VMs, Microsoft Entra ID (this is Azure AD’s new name!) or using Bastion.
And we don’t do that because we just don’t care about security, but because we’re Dynamics 365 people, and sometimes we might lack the knowledge in other things. If you’re lucky, you’ll have an in-house security team that’ll take care of that, otherwise we need to train ourselves a bit.
This is the first time I’ve used Microsoft Sentinel, and I’m for sure missing on a lot of things and features. Time to learn!
What is Microsoft Sentinel?
Let me repeat: this feature is in preview as of July 2023.
Microsoft Learn defines Sentinel as:
Microsoft Sentinel is a scalable, cloud-native solution that provides:
- Security information and event management (SIEM)
- Security orchestration, automation, and response (SOAR)
Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise. With Microsoft Sentinel, you get a single solution for attack detection, threat visibility, proactive hunting, and threat response.
https://learn.microsoft.com/en-us/azure/sentinel/overview
Microsoft Sentinel makes it easy to collect security data across your organization, not only Dynamics 365 F&O! From devices, to users, to apps, to servers on any cloud. It uses the power of artificial intelligence to ensure you are identifying real threats quickly.
Microsoft Sentinel provides several capabilities, including but not limited to:
- Collect data at cloud scale across all users, devices, applications, and infrastructure, both on-premises and in multiple clouds.
- Detect previously undetected threats, and minimize false positives using Microsoft’s analytics and unparalleled threat intelligence.
- Investigate threats with artificial intelligence, and hunt for suspicious activities at scale, tapping into years of cybersecurity work at Microsoft.
- Respond to incidents rapidly with built-in orchestration and automation of common tasks.
Configuring Microsoft Sentinel for F&O
The process to configure Microsoft Sentinel for F&O is pretty straightforward and if you follow the official Microsoft Learn tutorial to deploy Microsoft Sentinel solution for Dynamics 365 Finance and Operations, you should have no issues, but I’ll follow the same steps.
Create a new Log Analytics Workspace
Go to the Azure portal and look for Microsoft Sentinel, click the “Create Microsoft Sentinel” button:
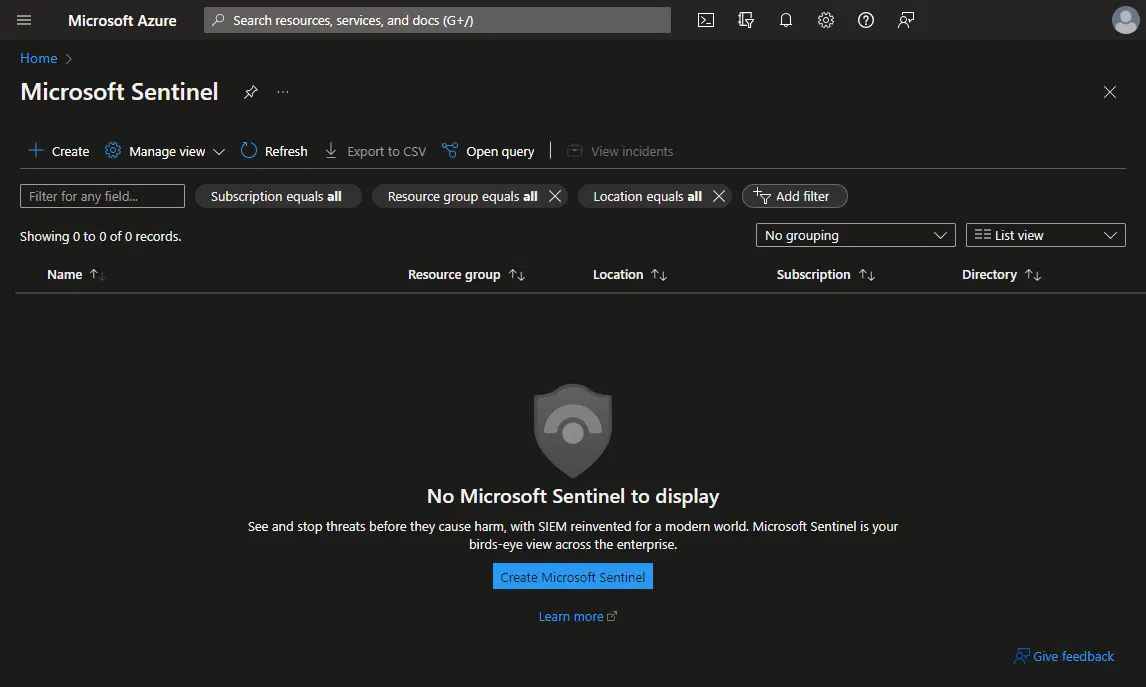
Microsoft Sentinel sort-of runs on top of a Log Analytics workspace. We use the Log Analytics workspace to ingest the data from our resources, then Microsoft Sentinel analyses that data. The create button will show the Log Analytics workspaces, if you have any:
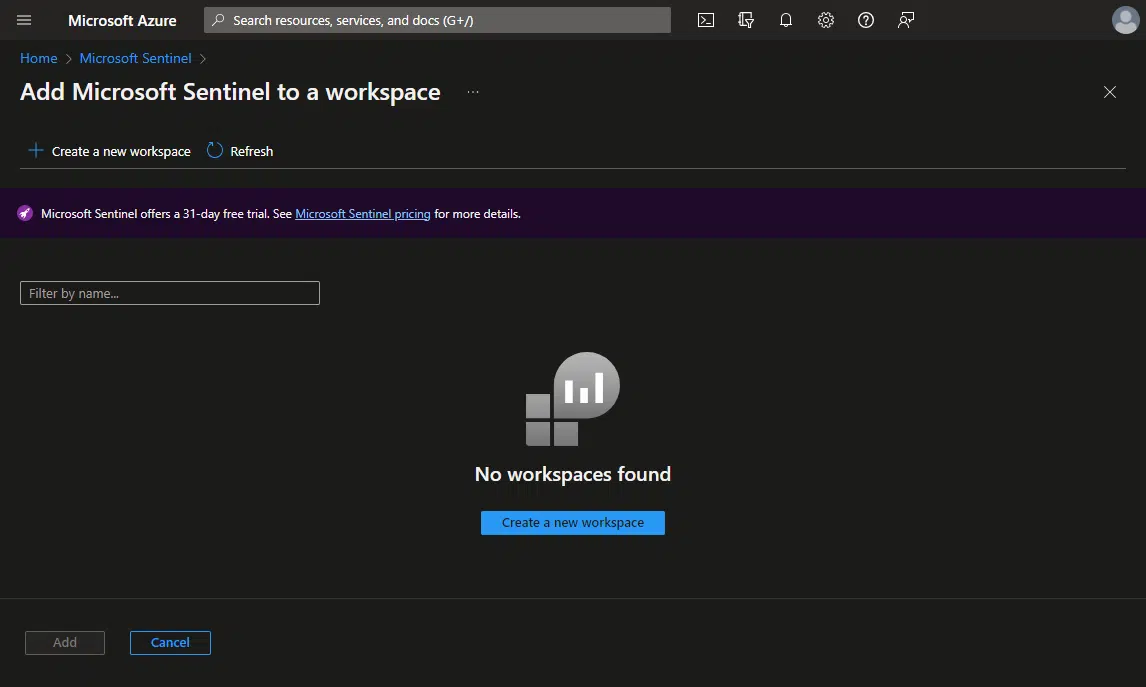
If you don’t have any, or want to create a new one, you must create a new one:
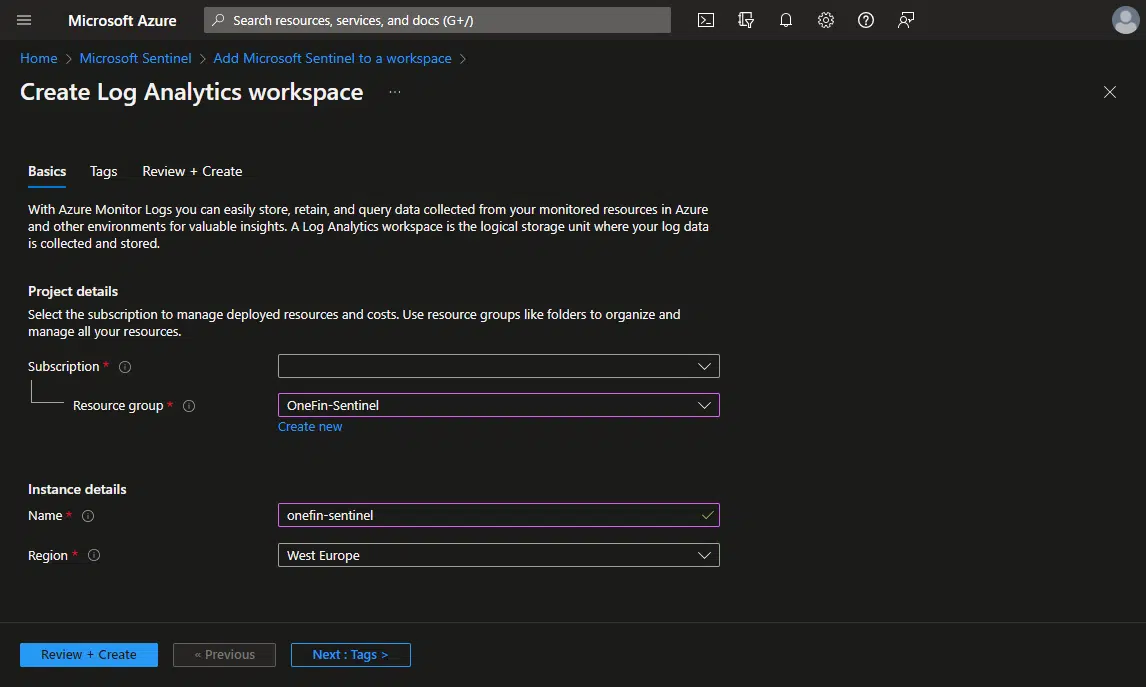
Give it a meaningful name, you can see in the image I’m calling it onefin-sentinel, but a better name would be onefin-sentinel-loganalytics.
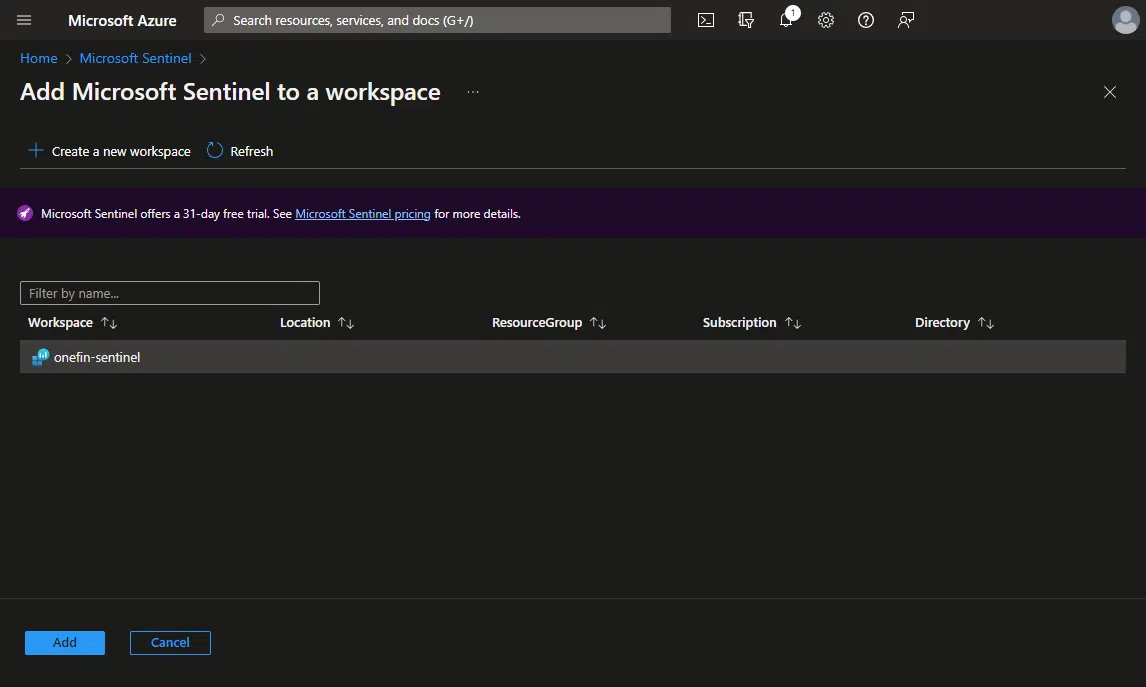
Add Microsoft Sentinel to the workspace
Once it’s created you will see it in the previous screen, if you don’t see it click the refresh button. Finally, select it and click the “Add” button in the bottom left corner.
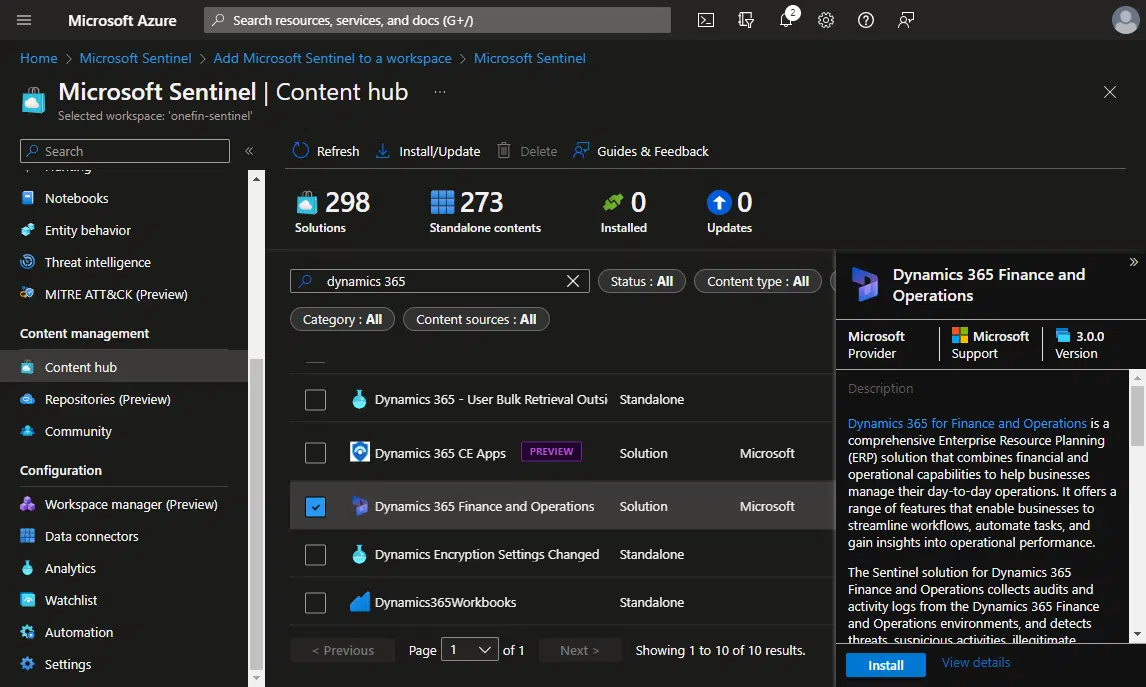
Install the F&O solution
When this is done, it will take you to the Microsoft Sentinel main screen. Now we need to install the F&O solution. In the left sidebar, look for “Content hub”, and then in the search bar look for Dynamics 365, you should see the one we want as “Dynamics 365 Finance and Operations”. Click the “Install” button in the lower right corner:
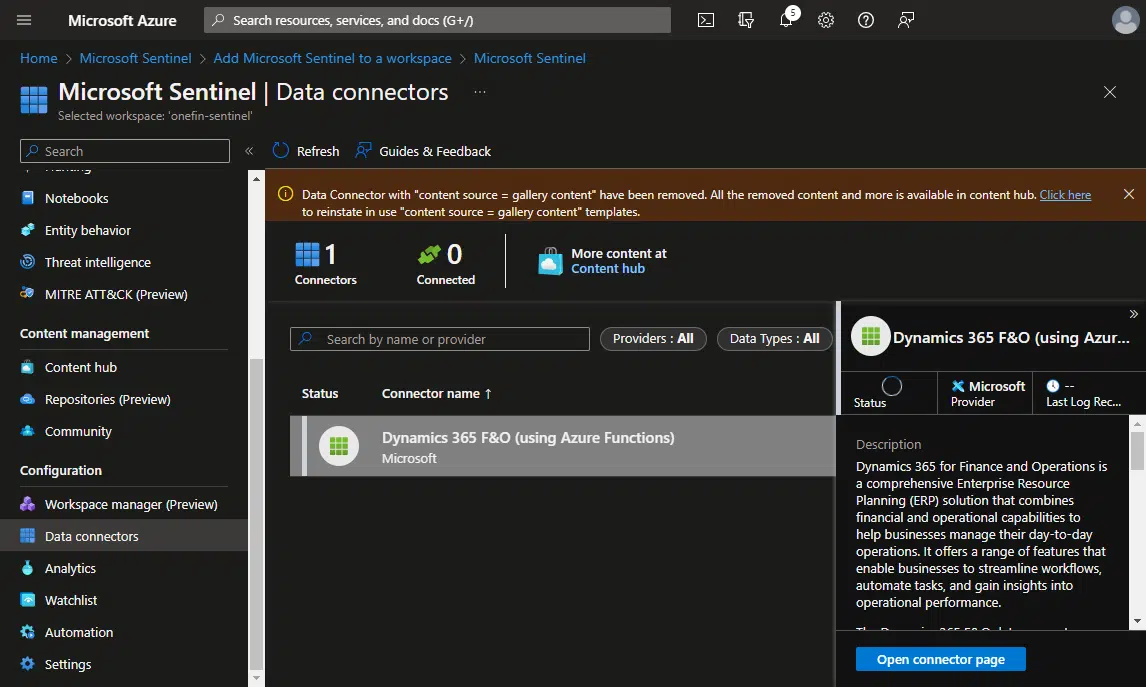
Install the F&O data connector
When the solution has finished installing, we need to add the data connector to F&O. In the left menu, go to the “Data connectors” section. You should already see the “Dynamics 365 F&O (using Azure Functions)” connector there. If it’s not there, use the search bar or try cleaning the filters:
Click the “Open connector page” button in the lower right corner. You will see this:
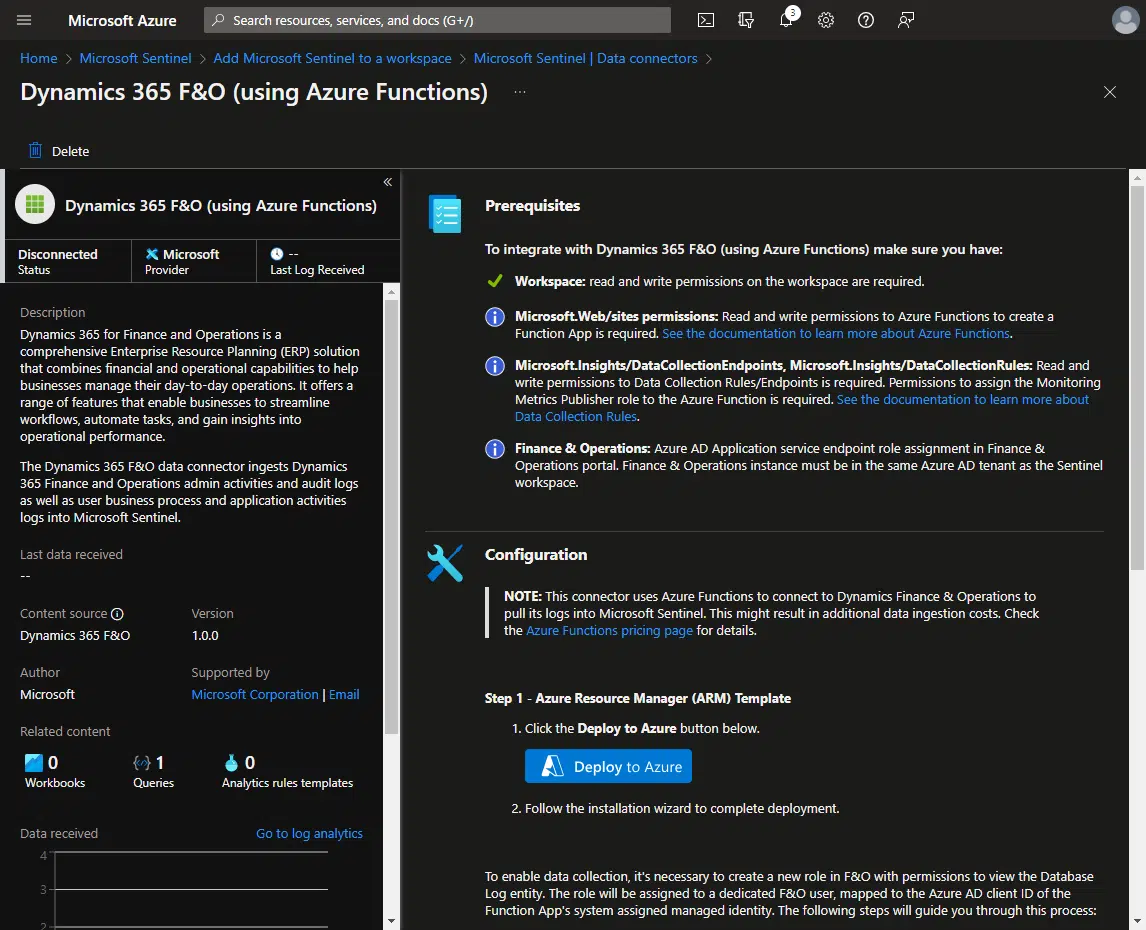
The data collection is done using an Azure Function. Don’t worry, it will be deployed using an ARM template. We just need to click the blue “Deploy to Azure” button, a new tab will open:
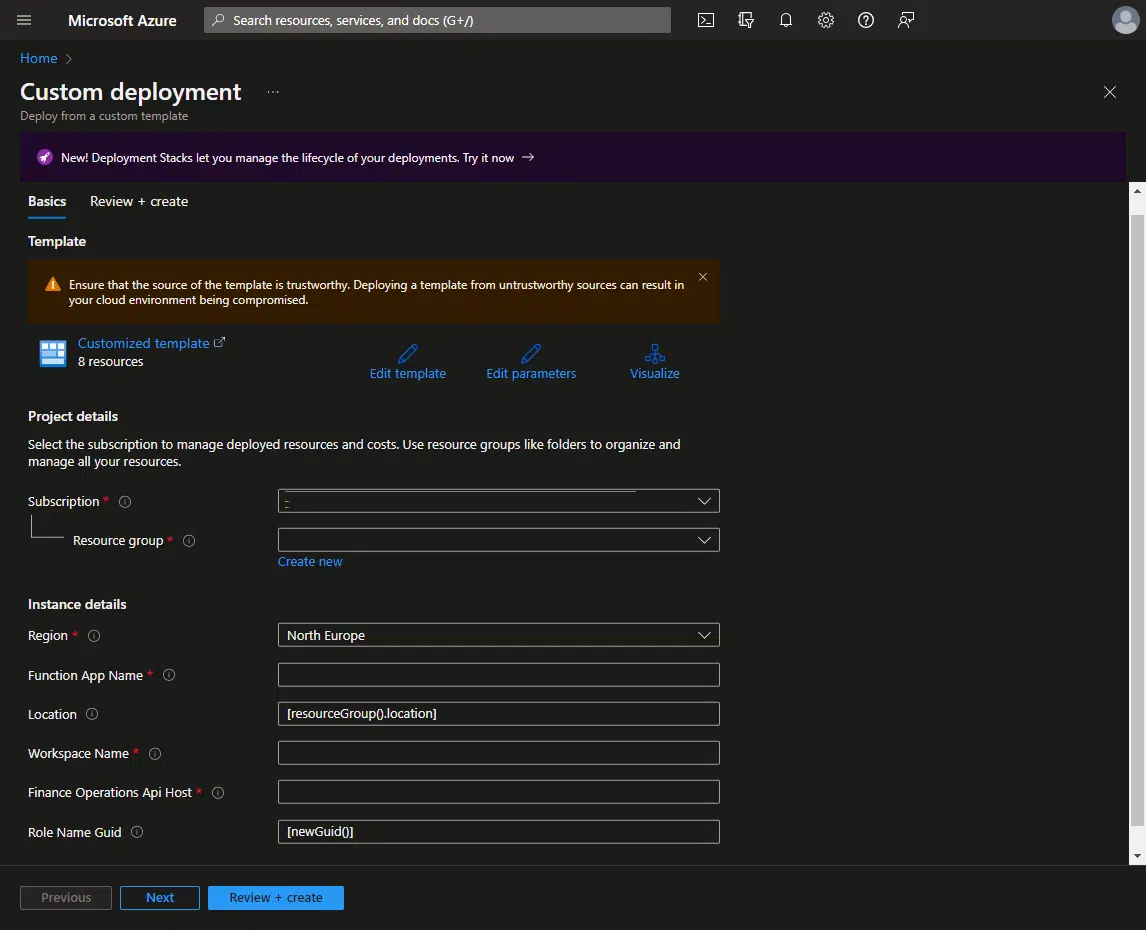
We need to complete the information in the template fields:
- Function App Name: the name of the Azure Function app, remember that it should be meaningful and describe what it is. Like d365fo-sentinel-app.
- Workspace Name: the Log Analytics workspace name we created in the first steps.
- Finance Operations Api Host: the URL of your Dynamics 365 F&O instance.
Click the “Review + create” button, and once everything has been validated, the “Create” button.
This will take a bit longer than the previous steps, but not much, I’d say less than 5 minutes.
Get the function Managed Identity
Head to the Azure AD section in the Azure portal. Yes, the name has changed, but not all the branding is ready yet. Navigate to the “Enterprise Applications” section. We have to remove the filter on the image below:
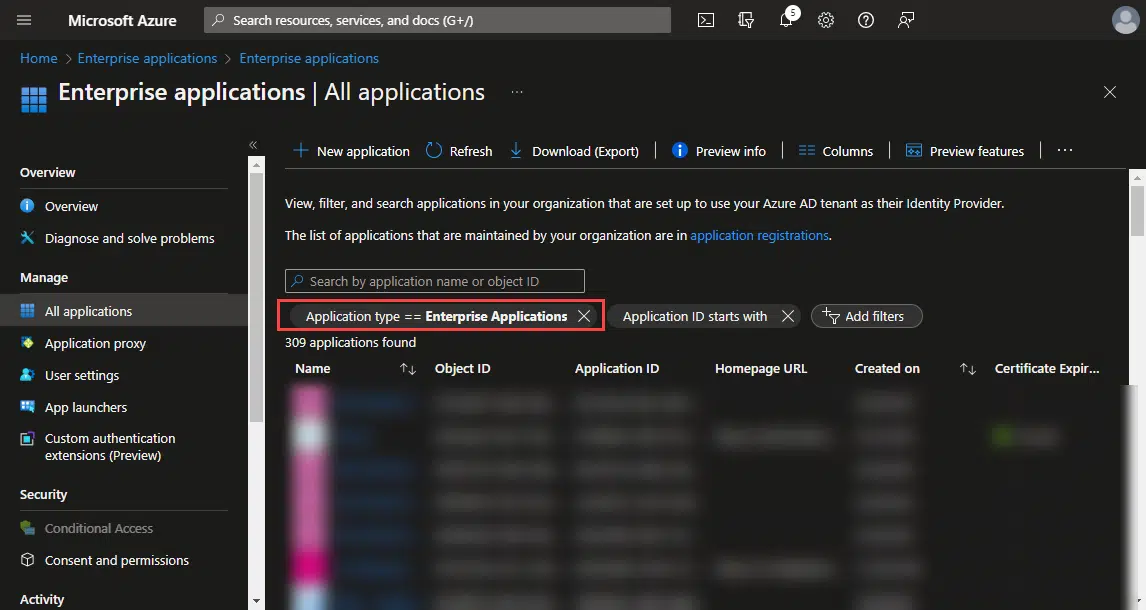
And then add a new filter to display only the managed identities apps:
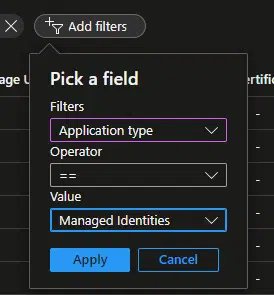
In the search bar look for your Azure Function app name:
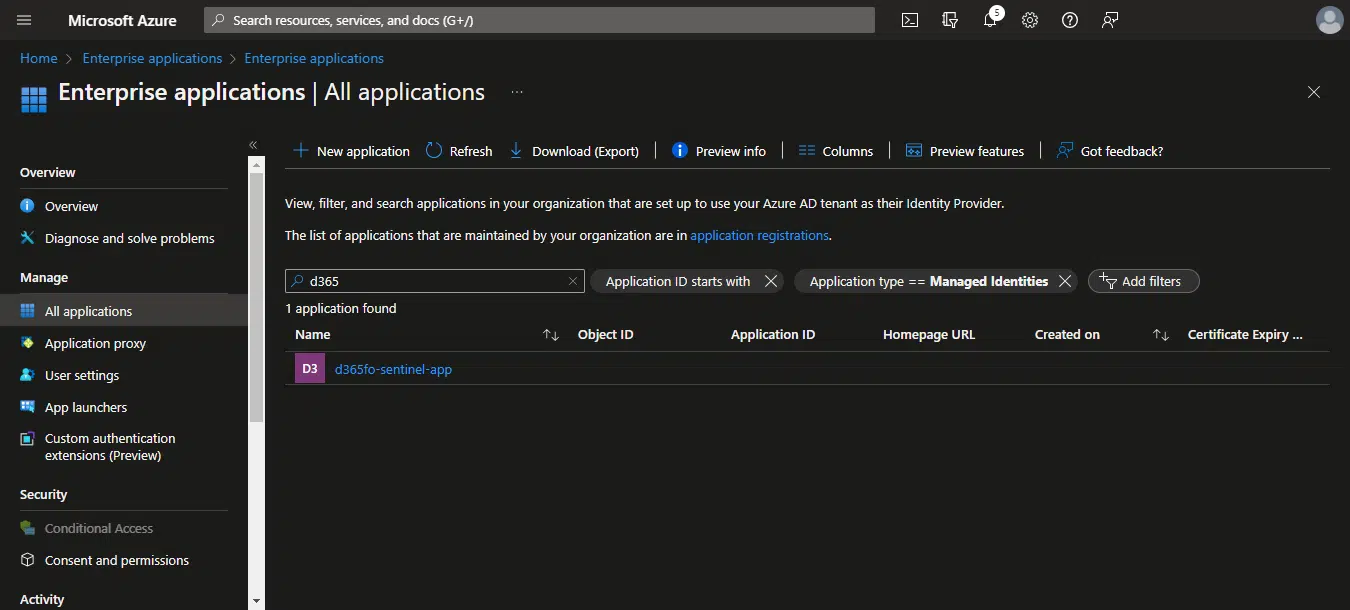
And finally, copy its Application ID. Now we’re headed to the F&O interface.
Create a new security role
Go to System administration -> Security -> Security configuration, and create a new role.
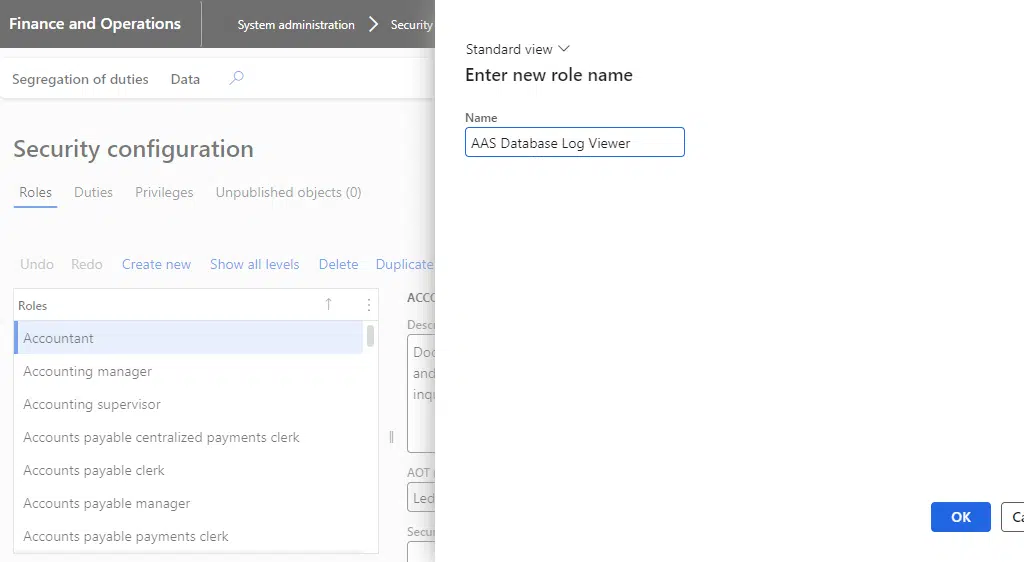
Now click on Privileges under the references grid, and click the “Add references” button:
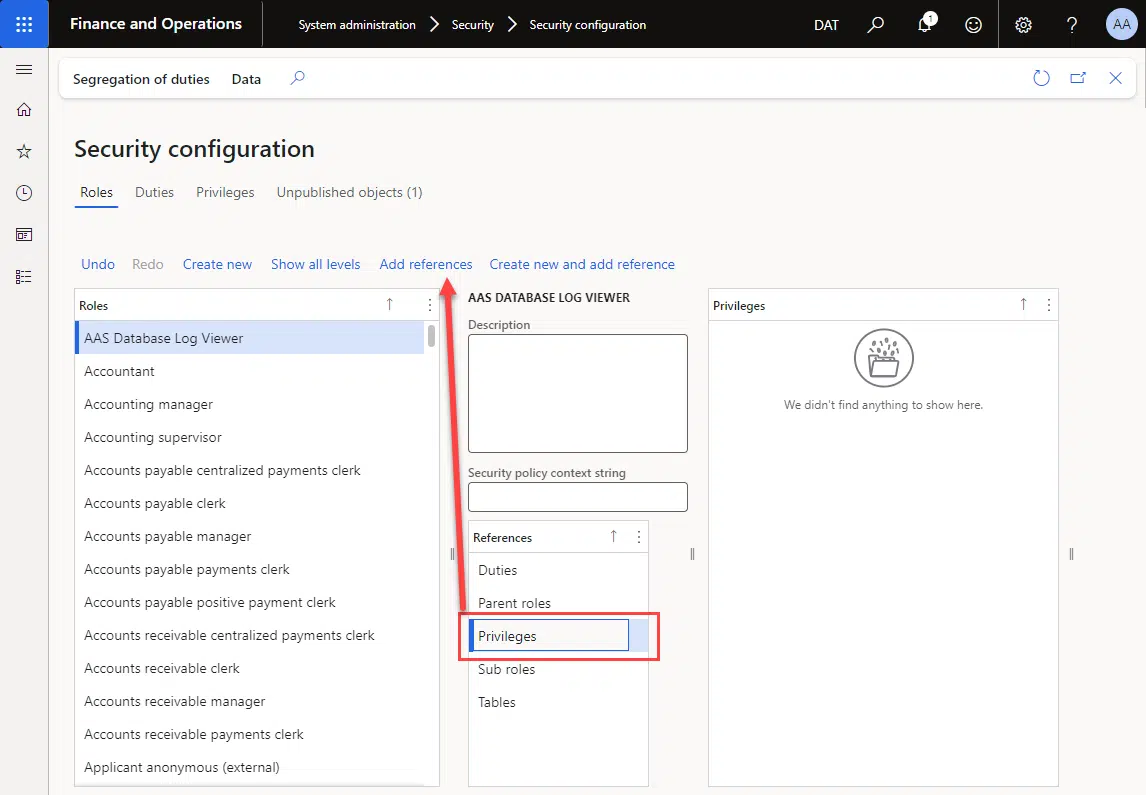
In the list, filter on the name and look for “Database log”. Add the “Database log Entity View” privilege.
Finally, publish the security objects. Go to the “Unpublished objects” tab, select the new role we just created, and click the “Publish selection” button. You can use the “Publish all” option if you wish and have no other pending changes:
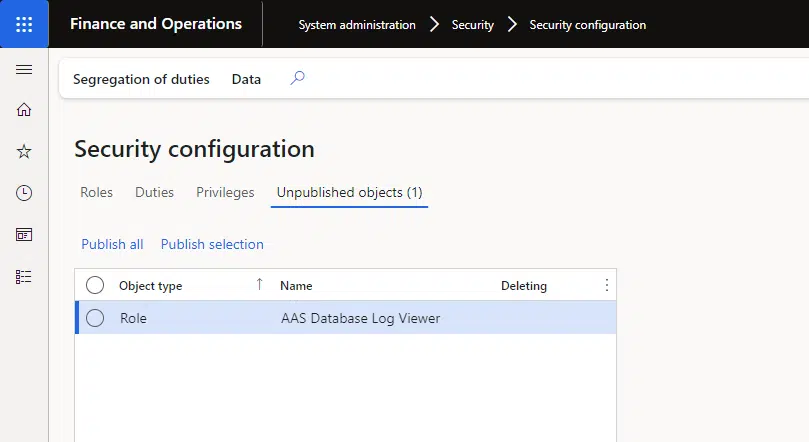
Note: if you’re not doing this for the production environment, it’s better to create the role and add the privilege in Visual Studio. If a DB refresh is done to the environment you’re using, the role created from the Dynamics 365 F&O UI will be gone.
Create a new user
Or use an existing one if you want. This user will be assigned the role we’ve created and used in the Azure Active Directory applications form.
If you use an existing user, make sure it’s not a superuser or system administrator.
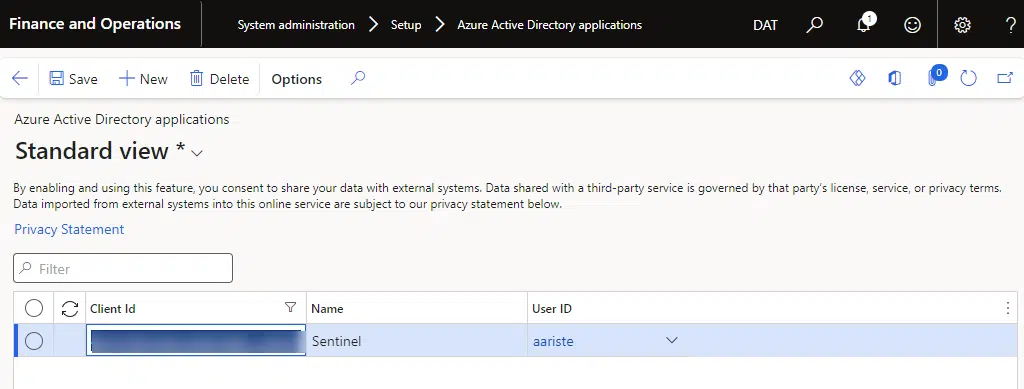
Add a new Azure AD application
Now, using the Application ID we copied before from the Azure Function managed identity, create a new record in the Azure Active Directory applications form, and use the new user we’ve just created as the User ID.
We’ve configured everything. Microsoft Sentinel is ready to ingest and analyze data from our Dynamics 365 F&O instance. But which data is monitored? Now, this is going to be interesting…
Now, the part that I don’t like…
You might’ve already noticed and already know where I’m going. When we created the new role, we added the privilege to read the database log entity, remember?
It’s not a surprise, the monitoring in Microsoft Sentinel for F&O is using the database log!! And what is wrong with the database log? Possible performance issues!!
So, in my opinion, this restricts a bit what we can do with Microsoft Sentinel to:
- Parameter tables
- Master data tables
- Other tables during a short period of time
And of course, we can forget about transaction tables. At least, it’s not possible to add new tables to the database log until you configure the cleanup log batch job.
Add whichever table you want to monitor. I’ve chosen the Bank Accounts as in the Learn tutorial. When the Azure Function app triggers, which does every 10 minutes, we will see the changes in the Logs section:
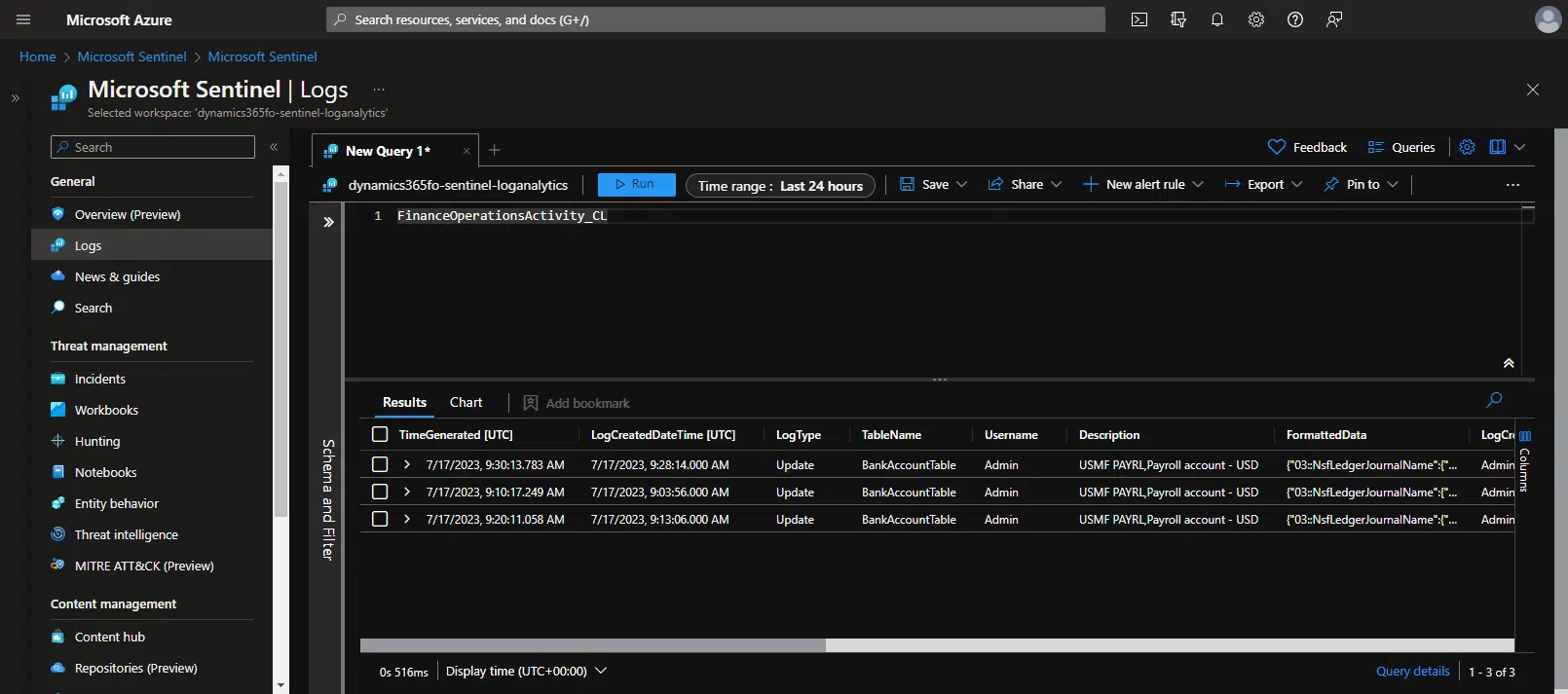
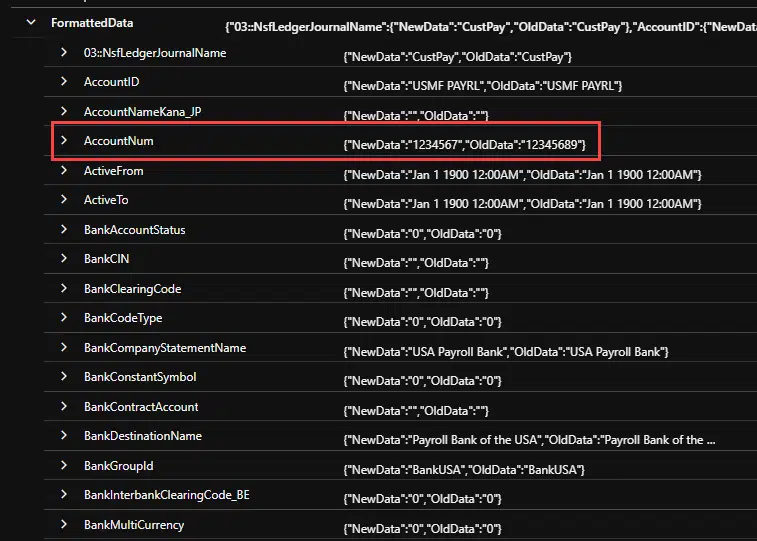
And in the query editor we look for the FinanceOperationsActivity_CL logs as in the image above, we will see the records for the changes done. And inside the “FormattedData” node we can see all the fields of the table that we’re logging, with their old and new value:
What does Microsoft Sentinel offers out-of-the-box for F&O?
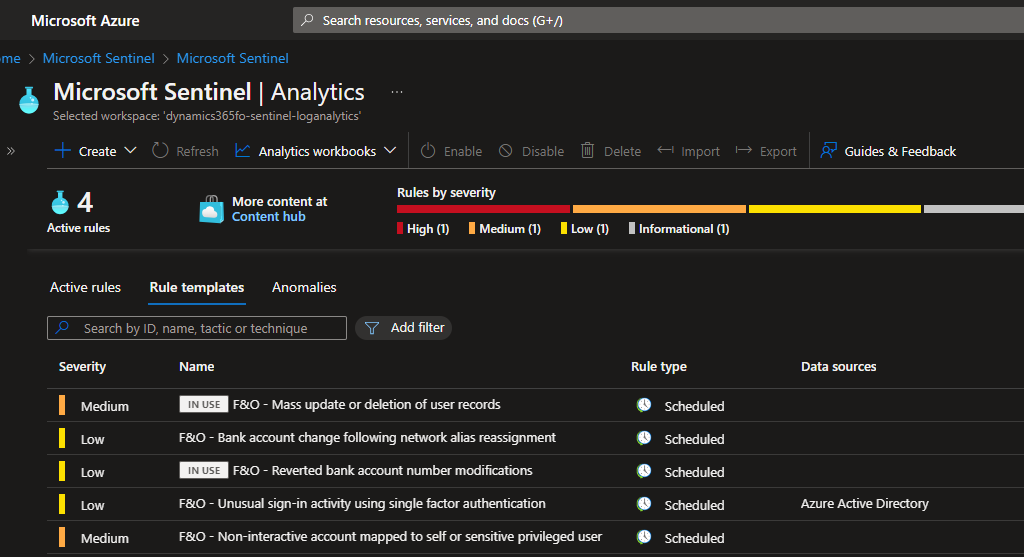
The solution we installed in the first steps includes a small set of rule templates that can be enabled and used with no other setup needed:
| Rule name | Description |
| F&O – Non-interactive account mapped to self or sensitive privileged user | Identifies changes to Azure AD Client Apps registered for Finance & Operations, specifically when a new client is mapped to a predefined list of sensitive privileged user accounts, or when a user associates a client app with their own account. To modify the list of sensitive privileged accounts, change the “priviliged_user_accounts” variable in the rule query. (Refer to the example in the rule query) |
| F&O – Mass update or deletion of user account records | Identifies large delete or update operations on Finance and Operations user records based on predefined thresholds. Default update threshold: 50 Default delete threshold: 10 |
| F&O – Bank account change following network alias reassignment | Identifies updates to bank account number by a user account which his alias was recently modified to a new value. |
| F&O – Reverted bank account number modifications | Identifies changes to bank account numbers in Finance & Operations, whereby a bank account number is modified but then subsequently reverted a short time later. |
| F&O – Unusual sign-in activity using single factor authentication | Identifies successful sign-in events to Finance & Operations and Lifecycle Services using single factor/password authentication. Sign-in events from tenants not using MFA, coming from an Azure AD trusted network location, or from geolocations seen previously in the last 14 days are excluded. This detection uses logs ingested from Azure Active Directory. Therefore, you should enable the Azure Active Directory data connector. |
These alert templates can be found under the Analytics menu, in the Rule templates tab:
This alerts can create incidents, which for example we can later use in a Logic App (there’s no Microsoft Sentinel connector for Power Automate), or can send notifications from Azure to administrators.
What happens behind the scenes?
I’ll provide a short explanation as a high-level overview of how all the elements we’ve deployed and configured work.
As we’ve seen, all of this depends on the database log functionality in Dynamics 365 Finance and Operations. Then there’s an Azure Function that runs on a schedule and will query the OData endpoint for the database log entity. That’s why we need to configure the managed identity of the Azure Function in the AD applications form.
And it’s the Azure Function the one that’s responsible to send the data to the Log Analytics Workspace, which is later analized by Microsoft Sentinel.
Some final thoughts
I do see the value of Microsoft Sentinel in securing your Azure AD Microsoft Entra ID. For F&O, with the functionality I’ve described here, and what I’ve been able to test… to me, it feels like, in simple scenarios, we’re using a sledgehammer to crack a nut. If you only want to track field changes, you can use the standard alerts’ functionality.
However, for complex scenarios, Microsoft Sentinel offers more advanced rules, like checking for mass updates, or field values being changed after a user has an updated network alias and therefore a different login. This is something that really does add a value to your security strategy.
As I said, this is the first time I’ve used Microsoft Sentinel, so I’m probably missing on something, I promise I’ll keep on investigating.





